Summary
Public Key Infrastructure (PKI) is a common authentication mechanism. Instead of knowing a secret like a password or PIN, it relies on a trusted entity pre-authenticating others and using public key cryptography to provide proof of authentication. The most common example would be secure web traffic over TLS. Another is using client certificates to log in to services such as a VPN.
While Microsoft Windows Server comes with PKI applications, this discussion will focus on Linux and free alternatives - specifically OpenSSL.
Background
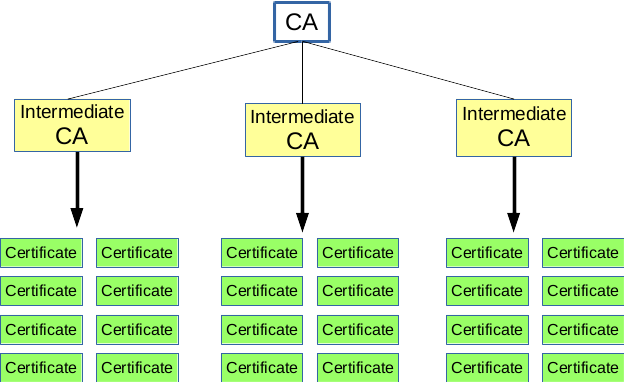
Certificate Authority Architecture
Who do you trust? To start with, you must be trust the manufacturer of your computer. Also whover made your operating system, browser, and everyone they trust. Take a look at the long list of Certificate Authorities (CA) that come preloaded at each step. Do you trust that foreign CA? Do you need to? If not, why enable it? The usual answer is convenience.
Process
The CA generates a public & private key pair on a very secure system. When not being used this should be stored physically offline somewhere safe. By various standards, it's actually stored in a Hardware Security Module (HSM). A self-signed certificate is generated for this root CA key pair. This certificate is widely distributed and the thing that everyone trusts.
Unless you're setting up PKI for an extremely small group, you never use the CA key pair in normal operation. The reason is there's no method to easily invalidate this CA certificate. You would need to have all users manually do that or rely on your IT automation. Of course, if that relied on PKI, you're back to manually doing this on all machines.
One or more 'intermediate' CA key pairs and certificates are generated. These are signed by the root CA and have delegated CA privileges. Perhaps one per physical location or type of certificates it will sign. Maybe a special one to generate Certificate Revocation Lists (CRLs). If you're up to a challenge it could be tied into an Online Certificate Status Protocal (OCSP) server.
These intermediate CAs then validate and sign individual certifictes for others. In most cases it is fully automated (see Automated Certificate Management Environment ACME). For small groups it would still be mostly manual. It is not too difficult to configure and script for a small group - the use case we will be discussing. Furthermore the examples here will not include this level of intermediate CAs to keep it less complicated.
Key Generation
If doing this 'for real' make sure you are generating good keys! Generating a key within a VM is not a good idea. The amount of entropy you get from a VM instance is questionable as well as the source of that entropy. It is highly recommended to use a local machine disconnected from the network to generate your keys. Preferably with 'rng-tools' installed and entropy gathered from your TPM or CPU hardware extended functionality.
Future
Why use PKI and CAs? This is so convoluted! A good alternative that has been proposed is to distribute web page certificates (actually just the public key) over DNS. Each user is already trusting their DNS to respond with the correct IP address, or a man-in-the-middle attack becomes much easier. Using DNSSEC and trusted DNS servers it would be reasonable to distribute both CRLs and certificates. Take a look at RFC 4438 (February 2006). I expect this hasn't become a standard yet since too much money has been poured into CAs and their tight relationships to browsers and operating systems. A different standard 'DANE' RFC 6698 was proposed in August of 2012. It also has not gained traction of major browser developers. Is this because of inertia, kickbacks from CAs to browsers distributing their certificate, or something else? For non-savvy users DANE could be a problem. It would mean whoever controls your DNS now can potentially spy and man-in-the-middle your 'secure' web connections. As for most this is an ISP or other corporation, you're really just trusting a different set of actors.
Configure and Use OpenSSL Certificate Authority
Using your favorite Linux distibution, install the OpenSSL package. This example will be specific to Debian, but mostly carry over to others.
apt install opensslYou can use the default configurations that come with this package. I will be describing a stripped down set to get you up and running quickly. We're going to use a separate directory to keep all our modified files in one place. This requires setting the environment variable OPENSSL_CONF=/var/ca/openssl.cnf This is the directory structure we will be using:
/var/ca/openssl.cnf - configuration file
/var/ca - root of the CA
./newcerts/ - where new certs are kept
./private/ca_key.pem - where we keep our private key
./cacert.pem - our CA cert
./index.txt - index of certs signed
./crlnumber - CRL number of the current crl
Generate CA public/private key
openssl genrsa -out /var/ca/private/ca_key.pem 4096Make CA certificate
openssl req -x509 -out /var/ca/cacert.pem
For advanced use... Try setting up your own OSCP responder: http://isrlabs.net/wordpress/?p=169
Distributing and Using your CA Certificate
To install in Firefox:
- Preferences -> Advanced -> Certificates -> View Certificates
- Import. Choose your ''cacert.pem'' file.
Set up Apache with your Certificate
If Apache is not already installed:
apt install apache2Generate your public/private key
openssl genrsa /etc/ssl/private/apache.key 4096Make a Certificate Signing Request
openssl req -new -key /etc/ssl/private/apache.key -out apache.csrSend CSR to CA and get it signed
openssl ca -in ./apache.csr out ./apache.crtInstall certificate in apache and configure apache
For advanced use... Try stapling OSCP responses from Apache: https://httpd.apache.org/docs/2.4/ssl/ssl_howto.html